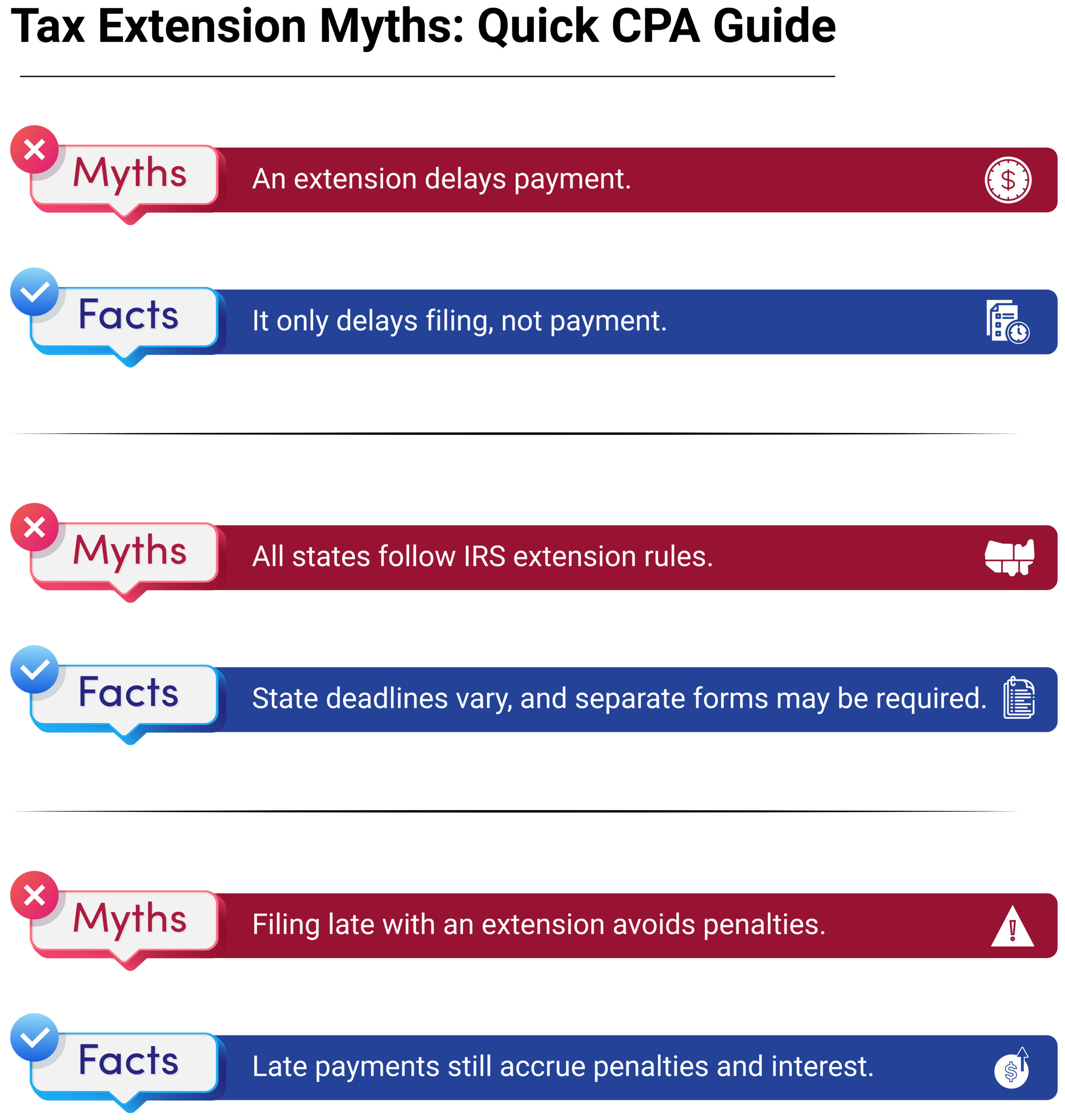
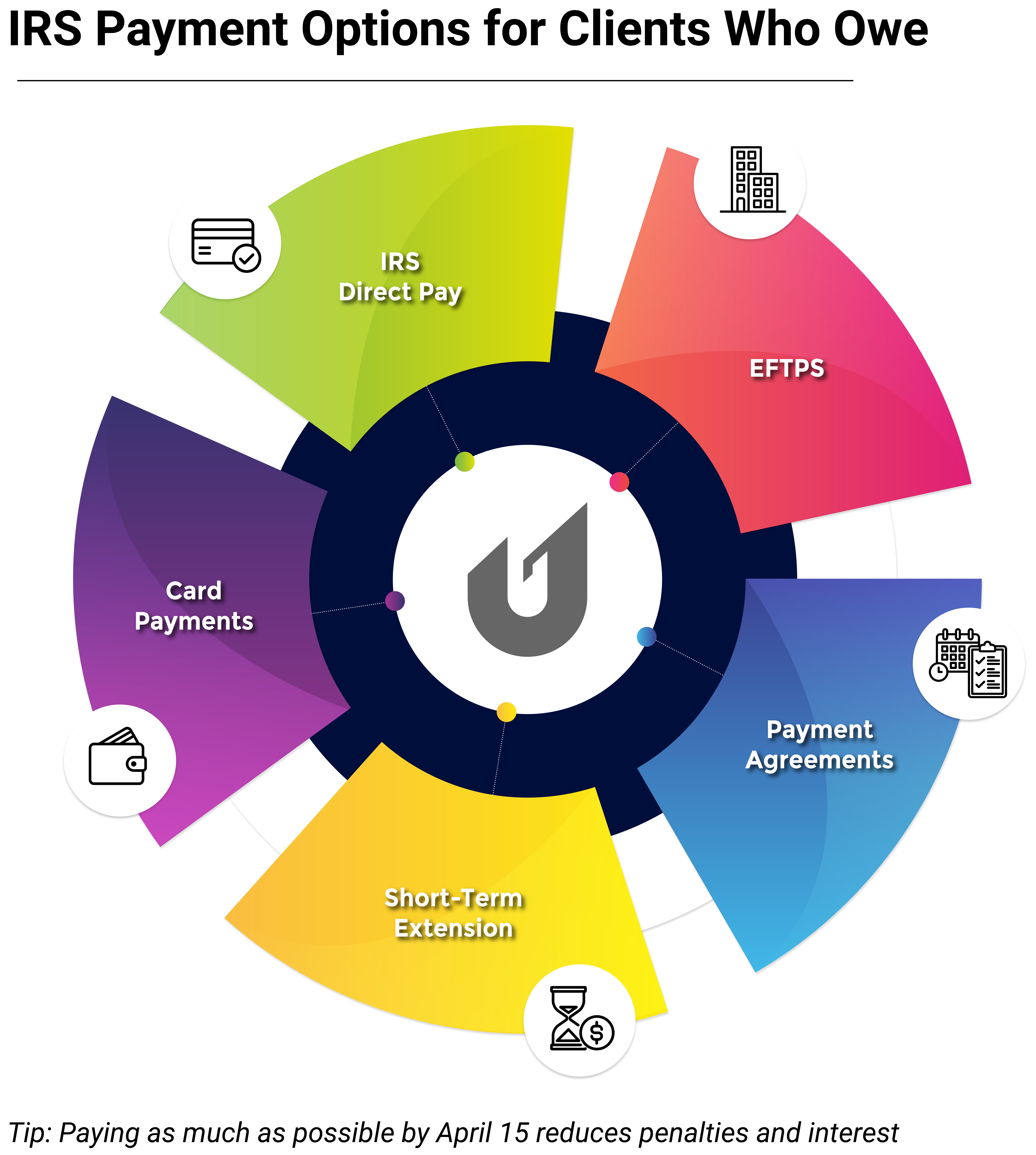
What Is an AI-Ready Professional?
The accounting profession is at a turning point. Over the past decade, the industry has experienced a steady decline in new talent entering the field, alongside a wave of retirements that shows no signs of slowing
At the same time, client expectations have shifted dramatically. Business owners are no longer satisfied with clean books and timely tax filings. They want insight, strategic guidance, and leadership. Layer on the rapid advancement of artificial intelligence, and it’s clear that firms must rethink how they operate. The answer is not choosing between technology and people. It’s developing professionals who know how to bring the two together. That is what it means to be an AI-ready professional.
The Talent Crisis is Real
The accounting workforce is shrinking. Fewer students are pursuing accounting degrees, CPA exam participation is down, and more than 75% of current CPAs are expected to retire within the next 15 years. At the same time, burnout remains high. Many accountants are overwhelmed by compliance work, long hours, and outdated operating models.
This isn’t a temporary staffing shortage. It’s a structural shift.
Firms can’t solve this by simply hiring locally. The depth of available talent isn’t there. Nor can they rely on AI alone to close the gap. That approach creates a different set of problems. The solution isn’t choosing between people and technology. It’s building a smarter model that leverages both.
AI is Powerful, But Not Perfect
AI tools are becoming more capable by the day. They can:
- Generate personalized client organizers
- Read documents and create workpapers
- Prepare draft tax returns
- Automate repetitive compliance tasks
2026 Keynote Slide Deck- Unison…
This saves time. It increases efficiency. It empowers teams to do more with fewer manual steps.
But AI is not flawless.
Accounting is detail-driven. One incorrect calculation or misinterpretation can change an outcome, and damage trust. Even the most advanced systems require human oversight. As Donny Shimamoto, Founder of the Center for Accounting Transformation, puts it: “AI can assist, but it won’t replace the professional judgement of a CPA.”
AI handles the mechanics. Professionals provide the judgment. That distinction matters.
What Clients Expect Today
Client expectations continue to evolve. Businesses want more than compliance services; they expect strategic advice, faster insights into what is happening inside their organizations, and proactive leadership that helps them anticipate challenges before they arise.
If firm leaders remain buried in routine compliance tasks, they simply do not have the bandwidth to provide that level of guidance. To meet modern expectations, firms must create capacity in smarter ways.
From Offshore 1.0 to Offshore 2.0
This is where the evolution of offshore staffing becomes important. Early offshore models focused heavily on cost reduction and transactional support.
This new model is about:
- Highly skilled, AI-ready professionals
- Strategic alignment with firm goals
- Dedicated resources, not shared labor
- Increasing leadership bandwidth
2026 Keynote Slide Deck- Unison…
This approach emphasizes dedicated resources, strong security, cultural integration, and long-term partnership. It is about expanding a firm’s capabilities, not replacing its people.
AI-ready Professionals Elevate Technology
An AI-ready professional understands how to oversee, leverage, and quality-check AI systems.
Imagine this workflow: AI gathers documents, sends reminders to clients, builds workpapers, and prepares a draft return. By the time a human touches the file, much of the administrative effort is complete.
That’s where the AI-ready professional steps in.
They:
- Review and validate AI outputs
- Apply tax strategy and accounting expertise
- Ensure compliance and quality
- Identify advisory opportunities
- Protect client trust
The firm’s final reviewer then focuses on high-level review and client delivery.
This layered model creates two major outcomes:
1. Leadership regains time and mental space.
2. Firms can scale without being constrained by local hiring shortages
2. Firms can scale without being constrained by local hiring shortages
The Future Belongs to Firms That Evolve
At Unison Globus, we believe the future of accounting firms lies in combining technology, well-defined processes, and highly skilled, accountable talent working in unison.
An AI-ready professional is not someone replaced by technology, nor someone competing against it. It is someone who understands how to oversee, leverage, and elevate AI to create better outcomes for clients while restoring balance for firm leadership. The firms that thrive in 2026 and beyond will blend AI-driven automation, strategically integrated offshore talent, and advisory-focused leadership into a smarter, leaner operating model.
If you are ready to move from reactive to proactive, to scale without sacrificing quality or well-being, connect with Unison Globus and let us help you build the bridge to a stronger future.

 [gtranslate]
[gtranslate]